Page 59 - EE Times Europe Magazine – November 2023
P. 59
EE|Times EUROPE 59
U.K. Conference Accelerates Post-Quantum Cryptography Standards Review Process
For reader inquiries and address changes,
please contact: christiane.lockner@aspencore.com
To unsubscribe, please go to:
www.eetimes.eu/unsubscribe/
Aspencore Media GmbH
Frankfurter Straße 211
63263 Neu-Isenburg
Germany
EE TIMES EDITORIAL MANAGEMENT
Brett Brune, Editor-in-Chief, EE Times,
brett.brune@aspencore.com
Anne-Françoise Pelé, Editor-in-Chief, EE Times Europe,
afpele@aspencore.com
Echo Zhao, Chief Analyst, echo.zhao@aspencore.com
Yorbe Zhang, Head of AspenCore APAC,
yorbe.zhang@aspencore.com
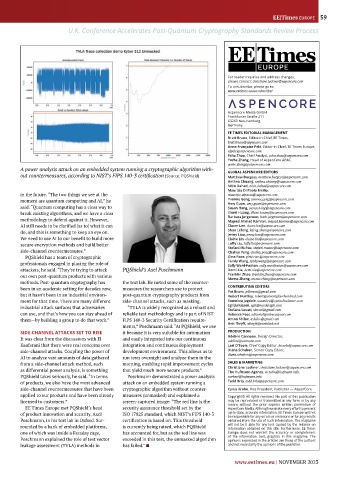
A power analysis attack on an embedded system running a cryptographic algorithm with- GLOBAL ASPENCORE EDITORS
out countermeasures, according to NIST’s FIPS 140-3 certification (Source: PQShield) Matthew Burgess, matthew.burgess@aspencore.com
Anthea Chuang, anthea.chuang@aspencore.com
Nitin Dahad, nitin.dahad@aspencore.com
Maurizio Di Paolo Emilio,
in the future. “The two things we see at the maurizio.dipaolo@aspencore.com
moment are quantum computing and AI,” he Yvonne Geng, yvonne.geng@aspencore.com
Amy Guan, amy.guan@aspencore.com
said. “Quantum computing has a clear way to Susan Hong, susan.hong@aspencore.com
break existing algorithms, and we have a clear Illumi Huang, illumi.huang@aspencore.com
methodology to defend against it. However, Barbara Jorgensen, barb.jorgensen@aspencore.com
Majeed Ahmad Kamran, majeed.kamran@aspencore.com
AI still needs to be clarified [as to] what it can Clover Lee, clover.lee@aspencore.com
do, and this is something to keep an eye on. Shao Lefeng, lefeng.shao@aspencore.com
Jenny Liao, jenny.liao@aspencore.com
We need to use AI to our benefit to build more Elaine Lin, elaine.lin@aspencore.com
secure encryption methods and build better Luffy Liu, luffy.liu@aspencore.com
side-channel countermeasures.” Stefani Muñoz, stefani.munoz@aspencore.com
Challey Peng, challey.peng@aspencore.com
PQShield has a team of cryptographic Gina Roos, gina.roos@aspencore.com
professionals engaged in playing the role of Fendy Wang, fendy.wang@aspencore.com
Sally Ward-Foxton, sally.wardfoxton@aspencore.com
attackers, he said. “They’re trying to attack PQShield’s Axel Poschmann Demi Xia, demi.xia@aspencore.com
our own post-quantum products with various Franklin Zhao, franklin.zhao@aspencore.com
Momo Zhong, momo.zhong@aspencore.com
methods. Post-quantum cryptography has the test lab. He noted some of the counter-
been in an academic setting for decades now, measures the researchers use to protect CONTRIBUTING EDITORS
Pat Brans, pdbrans@gmail.com
but it hasn’t been in an industrial environ- post-quantum cryptography products from Robert Huntley, robert@seventyfourhundred.com
ment for that time. There are many different side-channel attacks, such as masking. Saumitra Jagdale, saumitra@opencloudware.com
industrial attack surfaces that adversaries “TVLA is widely recognized as a robust and Egil Juliussen, egil@norskeagle.com
Stefano Lovati, slovati@gmail.com
can use, and that’s how you can stay ahead of reliable test methodology and is part of NIST Rebecca Pool, editorial@rebeccapool.com
them—by building a group to do that work.” FIPS 140-3 Security Certification require- Anton Shilov, ashilov@gmail.com
ments,” Poschmann said. “At PQShield, we use Ann Thryft, athryft@earthlink.net
SIDE-CHANNEL ATTACKS SET TO RISE it because it is very suitable for automation PRODUCTION
It was clear from the discussions with El and easily integrated into our continuous Adeline Cannone, Design Director,
adeline@cannone.com
Kaafarani that there were real concerns over integration and continuous deployment Lori O’Toole, Chief Copy Editor, lotoole@aspencore.com
side-channel attacks. Coupling the power of development environment. This allows us to Diana Scheben, Senior Copy Editor,
AI to analyze vast amounts of data gathered run tests overnight and analyze them in the diana.scheben@aspencore.com
from a side-channel attack method, such morning, enabling rapid improvement cycles SALES & MARKETING
as differential power analysis, is something that yield much more secure products.” Christiane Lockner, christiane.lockner@aspencore.com
The Hufmann Agency, victoria@hufmann.info,
PQShield takes seriously, he said. “In terms Poschmann demonstrated a power analysis norbert@hufmann.info
of products, we also have the most advanced attack on an embedded system running a Todd Bria, todd.bria@aspencore.com
side-channel countermeasures that have been cryptographic algorithm without counter- Cyrus Krohn, Vice President, Publisher — AspenCore
applied to our products and have been already measures (unmasked) and explained a Copyright© All rights reserved. No part of this publication
licensed to customers.” screen-captured image: “The red line is the may be reproduced or transmitted in any form or by any
means without the prior express written permission of
EE Times Europe met PQShield’s head security assurance threshold set by the AspenCore Media. Although we make every effort to present
of product innovation and security, Axel ISO 17825 standard, which NIST’s FIPS 140-3 up-to-date, accurate information, EE Times Europe will not
be responsible for any errors or omissions or for any results
Poschmann, in his test lab in Oxford. Sur- certification is based on. This threshold obtained from the use of such information. The magazine
rounded by a bank of embedded platforms, is currently being raised, which PQShield will not be li able for any loss caused by the reliance on
information obtained on this site. Furthermore, EE Times
one of which was inside a Faraday cage, has accounted for, but as the red line was Europe does not warrant the accuracy or completeness
Poschmann explained the role of test vector exceeded in this test, the unmasked algorithm of the information, text, graphics in this magazine. The
opinions expressed in the articles are those of the authors
leakage assessment (TVLA) methods in has failed.” ■ and not necessarily the opinions of the publisher.
www.eetimes.eu | NOVEMBER 2023