Page 16 - 23_EETE_03
P. 16
16 EE|Times EUROPE
IoT Security: What’s Driving the Software-to-Hardware Shift?
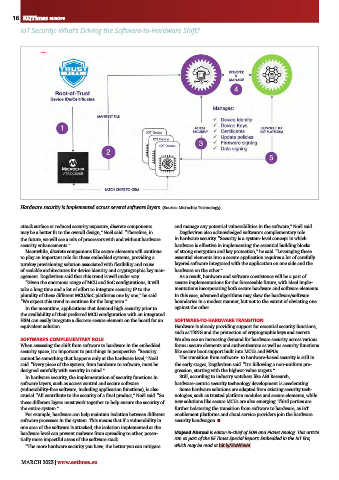
Hardware security is implemented across several software layers. (Source: Microchip Technology)
attack surface or reduced security exposure, discrete components and manage any potential vulnerabilities in the software,” Noël said.
may be a better fit to the overall design,” Noël said. “Therefore, in Dagdeviren also acknowledged software’s complementary role
the future, we will see a mix of processors with and without hardware in hardware security. “Security is a system-level concept in which
security enhancements.” hardware is effective in implementing the essential building blocks
Meanwhile, discrete companions like secure elements will continue of strong encryption and key protection,” he said. “Leveraging these
to play an important role for these embedded systems, providing a essential elements into a secure application requires a lot of carefully
turnkey provisioning solution associated with flexibility and reuse layered software integrated with the application on one side and the
of scalable architectures for device identity and cryptographic key man- hardware on the other.”
agement. Dagdeviren said that this trend is well under way. As a result, hardware and software coexistence will be a part of
“Given the enormous range of MCU and SoC configurations, it will secure implementations for the foreseeable future, with ideal imple-
take a long time and a lot of effort to integrate security IP to the mentations incorporating both secure hardware and software elements.
plurality of these different MCU/SoC platforms one by one,” he said. In this case, advanced algorithms may skew the hardware/software
“We expect this trend to continue for the long term.” boundaries in a modest manner, but not to the extent of obviating one
In the meantime, applications that demand high security prior to against the other.
the availability of their preferred MCU configuration with an integrated
HSM can easily integrate a discrete secure element on the board for an SOFTWARE-TO-HARDWARE TRANSITION
equivalent solution. Hardware is already providing support for essential security functions,
such as TRNG and the protection of cryptographic keys and secrets.
SOFTWARE’S COMPLEMENTARY ROLE We also see an increasing demand for hardware security across various
When assessing the shift from software to hardware in the embedded forms: secure elements and authenticators as well as security functions
security space, it’s important to put things in perspective. “Security like secure boot support built into MCUs and MPUs.
cannot be something that happens only at the hardware level,” Noël The transition from software- to hardware-based security is still in
said. “Every piece of the system, from hardware to software, must be the early stages, Dagdeviren said. “It’s following a non-uniform pro-
designed carefully with security in mind.” gression, starting with the highest-value targets.”
In hardware security, the implementation of security functions in Still, according to industry watchers like ABI Research,
software layers, such as access control and secure software hardware-centric security technology development is accelerating.
(vulnerability-free software, including application functions), is also Some hardware solutions are adapted from existing security tech-
crucial. “All contribute to the security of a final product,” Noël said. “So nologies, such as trusted platform modules and secure elements, while
these different layers must work together to help ensure the security of new solutions like secure MCUs are also emerging. Third parties are
the entire system.” further bolstering the transition from software to hardware, as IoT
For example, hardware can help maintain isolation between different enablement platforms and cloud service providers join the hardware
software processes in the system. This means that if a vulnerability in security bandwagon. ■
one area of the software is attacked, the isolation implemented at the
hardware level can prevent malware from spreading to other, poten- Majeed Ahmad is editor-in-chief of EDN and Planet Analog. This article
tially more impactful areas of the software stack. ran as part of the EE Times Special Report: Embedded in the IoT Era,
“The more hardware security you have, the better you can mitigate which may be read at bit.ly/3lxWhwV.
MARCH 2023 | www.eetimes.eu