Page 14 - 23_EETE_03
P. 14
14 EE|Times EUROPE
EMBEDDED WORLD 2023: SECURITY FOCUS
IoT Security: What’s Driving the
Software-to-Hardware Shift?
By Majeed Ahmad
he hardware choices for embedded security are growing dynamically as Semiconductors. “Counterfeit protection is a
the push for more secure IoT devices and applications shifts the security strong driver to defend the originality of the
products, as this can only be accomplished
implementation focus from software to hardware. The secure hardware through hardware.”
T technologies targeted at the internet of things include secure elements, In this regard, he also mentioned connected
hardware security modules (HSMs) and physically unclonable function (PUF) devices—complex systems in which software
operating at different layers of abstraction
capabilities. executes over hardware.
Shipments of secure hardware serving digital authentication and embedded Hardware security includes numerous
safety features and components: true
security will reach 5.3 billion by 2024, doubling the number of shipments in 2019,
random-number generation (TRNG), secure
according to ABI Research. “Hardware-based security offers better protection boot mechanisms, secure update, secure
from manipulation and interference than its software-based counterpart because debug, cryptographic acceleration, isolation of
sensitive and critical functions with security
it’s more difficult to alter or attack the physical device or data entry points,” said subsystems, tamper resistance and protection
Michela Menting, digital security research director at ABI Research. of secrets, tamper detection, on-the-fly mem-
ory encryption, process/functions isolation
Attack scenarios against embedded systems of an autonomous industrial robot or the and runtime integrity protection.
have increased in sophistication with increas- navigation system of an autonomous vehicle More importantly, the way security is
ing computing power, according to Nuri connected to the internet should be immedi- implemented is fundamental, Noël noted.
Dagdeviren, corporate vice president for the ately apparent. “Effective security solutions are the result
security products business unit at Microchip of a strict development process with clearly
Technology. “The range of defenses provided ANATOMY OF HARDWARE SECURITY defined design rules, multiple iterations of
by the hardware and software implemen- Hardware, which is more difficult to tamper careful review and full control over the many
tations differs significantly against these with than software, serves as the foundation sub-components involved in the design.”
evolving attack scenarios, and more and more of the complex systems that address security. That’s why security certification is critical,
applications justify the hardware implemen- It’s the layer on top of which all other layers he added. It provides design engineers with
tations,” he said. are built and mounted: firmware, operating an external proof point for the device’s level
For example, the importance of build- systems, connectivity libraries and applica- of security and makes it easier to compare
ing defenses against hacking an isolated tion software. security solutions.
thermostat or a car radio may not be a “This is the concept of the root of trust,”
priority concern, Dagdeviren said, whereas said Denis Noël, director of product mar- SECURITY EMBEDDED INTO SoCs
the importance of securing the integrity keting for secure authentication at NXP The key element of an information security
implementation is strong encryption with
a securely protected encryption key. Mod-
ern microcontrollers, secure elements and
integrated HSMs all provide strong encryption
capabilities.
“Secure elements and HSMs provide the
highest levels of protection for the encryp-
tion keys,” Dagdeviren said. “PUF is a unique
technique that overlays the key protection
capability on MCUs via modest incremental
implementation complexity.”
At the same time, security IP and
subsystems are being integrated into system-
on-chip designs. Many NXP processors today,
including the company’s i.MX 9 applications
processor series, come to market with inte-
grated security subsystems.
As Noël noted, however, there are tradeoffs
to integrating security directly in the pro-
cessors. For example, an integrated secure
subsystem will necessitate a large die.
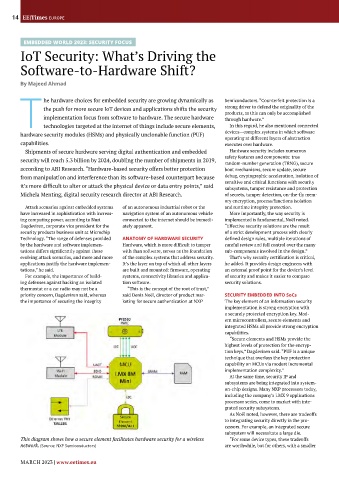
This diagram shows how a secure element facilitates hardware security for a wireless “For some device types, these tradeoffs
network. (Source: NXP Semiconductors) are worthwhile, but for others, with a smaller
MARCH 2023 | www.eetimes.eu