Page 45 - EE|Times Europe Magazine - December 2020
P. 45
EE|Times EUROPE 45
Real-Life Scenarios: How the Industrial Cloud Gets Hacked
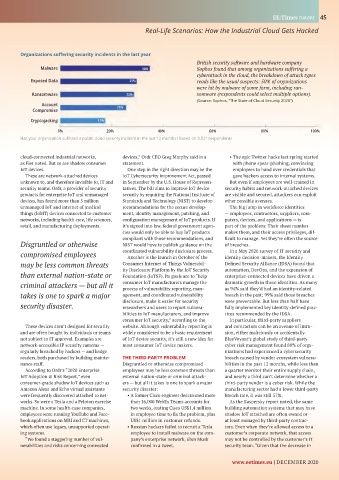
Organizations suffering security incidents in the last year
British security software and hardware company
Malware 34% Sophos found that among organizations suffering a
cyberattack in the cloud, the breakdown of attack types
Exposed Data 29% reads like the usual suspects: 50% of organizations
were hit by malware of some form, including ran-
Ransomware 28% somware (respondents could select multiple options).
(Source: Sophos, “The State of Cloud Security 2020”)
Account
Compromise 25%
Cryptojacking 17%
0% 20% 40% 60% 80% 100%
Has your organization suffered a public cloud security incident in the last 12 months? Based on 3,521 respondents
cloud-connected industrial networks, devices,” Ordr CEO Greg Murphy said in a • The epic Twitter hacks last spring started
as Fier noted. But so are shadow consumer statement. with phone spear-phishing, convincing
IoT devices. One step in the right direction may be the employees to hand over credentials that
These are network-attached devices IoT Cybersecurity Improvement Act, passed gave hackers access to internal systems.
unknown to, and therefore invisible to, IT and in September by the U.S. House of Represen- But even if employees are well-trained in
security teams. Ordr, a provider of security tatives. The bill aims to improve IoT device security habits and network-attached devices
products for enterprise IoT and unmanaged security by requiring the National Institute of are visible and secured, attackers can exploit
devices, has found more than 5 million Standards and Technology (NIST) to develop other possible avenues.
unmanaged IoT and internet of medical recommendations for the secure develop- The big jump in workforce identities
things (IoMT) devices connected to customer ment, identity management, patching, and — employees, contractors, suppliers, com-
networks, including health care, life sciences, configuration management of IoT products. If puters, devices, and applications — is
retail, and manufacturing deployments. it’s signed into law, federal government agen- part of the problem: Their sheer number
cies would only be able to buy IoT products makes them, and their access privileges, dif-
compliant with those recommendations, and ficult to manage. Yet they’re often the source
Disgruntled or otherwise NIST would have to publish guidance on the of breaches.
In a May 2020 survey of IT security and
compromised employees coordinated vulnerability disclosure process. identity decision-makers, the Identity
Another is the launch in October of the
may be less common threats Consumer Internet of Things Vulnerabil- Defined Security Alliance (IDSA) found that
than external nation-state or ity Disclosure Platform by the IoT Security automation, DevOps, and the expansion of
enterprise-connected devices have driven a
Foundation (IoTSF). Its goals are to “help
criminal attackers — but all it consumer IoT manufacturers manage the dramatic growth in these identities. As many
process of vulnerability reporting, man-
as 94% said they’d had an identity-related
takes is one to spark a major agement, and coordinated vulnerability breach in the past; 99% said those breaches
security disaster. disclosure, make it easier for security were preventable. But less than half have
researchers and users to report vulnera-
fully implemented key identity-defined prac-
bilities to IoT manufacturers, and improve tices recommended by the IDSA.
consumer IoT security,” according to the In particular, third-party suppliers
These devices aren’t designed for security website. Although vulnerability reporting is and contractors can be an avenue of intru-
and are often bought by individuals or teams widely considered to be a basic requirement sion, either maliciously or accidentally.
not subject to IT approval. Examples are of IoT device security, it’s still a new idea for BlueVoyant’s global study of third-party
network-accessible IP security cameras — most consumer IoT device makers. cyber risk management found 80% of orga-
regularly breached by hackers — and badge nizations had experienced a cybersecurity
readers, both purchased by building mainte- THE THIRD-PARTY PROBLEM breach caused by vendor ecosystem vulnera-
nance staff. Disgruntled or otherwise compromised bilities in the past 12 months, while less than
According to Ordr’s “2020 Enterprise employees may be less common threats than a quarter monitor their entire supply chain,
IoT Adoption & Risk Report,” even external nation-state or criminal attack- and nearly a third can’t determine whether a
consumer-grade shadow IoT devices such as ers — but all it takes is one to spark a major third-party vendor is a cyber risk. While the
Amazon Alexa and Echo virtual assistants security disaster: manufacturing sector had a lower third-party
were frequently discovered attached to net- • A former Cisco engineer deactivated more breach rate, it was still 57%.
works. So were a Tesla and a Peloton exercise than 16,000 WebEx Teams accounts for As the Kaspersky report noted, the same
machine. In some health-care companies, two weeks, costing Cisco US$1.4 million building automation systems that may have
employees were running YouTube and Face- in employee time to fix the problem, plus shadow IoT attached are often owned or
book applications on MRI and CT machines, US$1 million in customer refunds. at least managed by third-party contrac-
which often use legacy, unsupported operat- • Russian hackers failed to recruit a Tesla tors. Even when they’re allowed access to a
ing systems. employee to install malware on the com- customer’s corporate network, that access
“We found a staggering number of vul- pany’s enterprise network, Elon Musk may not be controlled by the customer’s IT
nerabilities and risks concerning connected confirmed in a tweet. security team. “Given that the decrease in
www.eetimes.eu | DECEMBER 2020