Page 50 - EE|Times Europe Magazine - December 2020
P. 50
50 EE|Times EUROPE
Protecting the Endpoint in IIoT: A Snapshot of Chip-Level Security
Infineon Technologies’ portfolio of security controllers to protect the from supply chain to device onboarding — through in-field updates
integrity and authenticity of embedded devices and systems includes and always-on firmware monitoring.
the OPTIGA TPM family. The OPTIGA TPM SLM 9670 is a quality- In October 2019, Micron introduced the Authenta key management
hardened trusted platform module for use in industrial applications service (KMS) platform to enable a cloud-first deployment model for
and based on a tamper-resistant secure microcontroller. As a turnkey a broad set of industrial applications. The platform allows installed
solution, it’s flashed with securely coded firmware according to the Authenta-enabled devices to be switched on through a cloud-based
latest Trusted Computing Group (TCG) Family 2.0 specifications. The service, mitigating some of the challenges and complexities related to
device is qualified according to the industrial JEDEC JESD 47 standard securing devices in a connected environment.
and is security-certified according to Common Criteria EAL4+.
Developers can implement a complete automated certificate issuance EMBEDDED SIM
and management solution for the factory floor based on the OPTIGA For applications such as remote condition monitoring, asset tracking,
TPM for private key storage together with an identity management and predictive monitoring, an industrial-grade embedded SIM (eSIM)
solution from Sectigo. on the chip can be a good approach. ST’s GSMA-compliant ST4SIM —
based on its ST33G secure MCU, featuring a
tamper-proof Arm SecurCore SC300 processor
and extra security features such as hardware
cryptographic accelerators — provides one
such solution in the form of both hardware
and software.
This solution uses partners Akessa,
Arm, and Truphone to provide and operate
device-onboarding and service-provisioning
platforms. The provisioning services enable
IoT devices containing the eSIMs to connect
automatically to cellular networks using flexi-
ble lifetime subscription management. ST said
its partners/operators can access hundreds of
cellular networks of all types, including 2G,
3G, 4G, low-power wide-area connectivity
(LTE CAT-M), and narrowband IoT (NB-IoT),
in large numbers of territories worldwide.
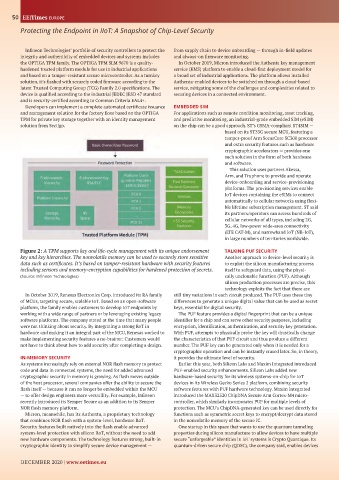
Figure 2: A TPM supports key and life-cycle management with its unique endorsement TALKING PUF SECURITY
key and key hierarchies. The nonvolatile memory can be used to securely store sensitive Another approach to device-level security is
data such as certificates. It’s based on tamper-resistant hardware with security features to exploit the silicon manufacturing process
including sensors and memory-encryption capabilities for hardened protection of secrets. itself to safeguard data, using the physi-
(Source: Infineon Technologies) cally unclonable function (PUF). Although
silicon production processes are precise, this
technology exploits the fact that there are
In October 2019, Renesas Electronics Corp. introduced its RA family still tiny variations in each circuit produced. The PUF uses these tiny
of MCUs, targeting secure, scalable IoT. Based on an open-software differences to generate a unique digital value that can be used as secret
platform, the family enables customers to develop IoT endpoints by keys, essential for digital security.
working with a wide range of partners or by leveraging existing legacy The PUF feature provides a digital fingerprint that can be a unique
software platforms. The company stated at the time that many people identifier for a chip and can serve other security purposes, including
were not thinking about security. By integrating a strong RoT in encryption, identification, authentication, and security key generation.
hardware and making it an integral part of the MCU, Renesas worked to With PUF, attempts to physically probe the key will drastically change
make implementing security features a no-brainer: Customers would the characteristics of that PUF circuit and thus produce a different
not have to think about how to add security after completing a design. number. The PUF key can be generated only when it is needed for a
cryptographic operation and can be instantly erased later. So, in theory,
IN-MEMORY SECURITY it provides the ultimate level of security.
As systems increasingly rely on external NOR flash memory to protect Earlier this year, both Silicon Labs and Maxim Integrated introduced
code and data in connected systems, the need for added advanced PUF-enabled security enhancements. Silicon Labs added new
cryptographic security in memory is growing. As flash moves outside hardware-based security for its wireless systems-on-chip for IoT
of the host processor, several companies offer the ability to secure the devices in its Wireless Gecko Series 2 platform, combining security
flash itself — because it can no longer be embedded within the MCU software features with PUF hardware technology. Maxim Integrated
— to offer design engineers more versatility. For example, Infineon introduced the MAX32520 ChipDNA Secure Arm Cortex-M4 micro-
recently introduced its Semper Secure as an addition to its Semper controller, which similarly incorporates PUF for multiple levels of
NOR flash memory platform. protection. The MCU’s ChipDNA-generated key can be used directly for
Micron, meanwhile, has its Authenta, a proprietary technology functions such as symmetric secret keys to encrypt/decrypt data stored
that combines NOR flash with a system-level, hardware RoT. in the nonvolatile memory of the secure IC.
Security features built natively into the flash enable advanced One startup in this space that wants to use the quantum tunneling
system-level protection with silicon RoT, without the need to add properties during silicon manufacture to allow devices to have multiple
new hardware components. The technology features strong, built-in secure “unforgeable” identities in IoT systems is Crypto Quantique. Its
cryptographic identity to simplify secure device management — quantum-driven secure chip (QDSC), the company said, enables devices
DECEMBER 2020 | www.eetimes.eu