Page 41 - EE|Times Europe Magazine - December 2020
P. 41
EE|Times EUROPE 41
SECURITY
Shifting to Cloud Makes Security More Difficult
By Ann R. Thryft
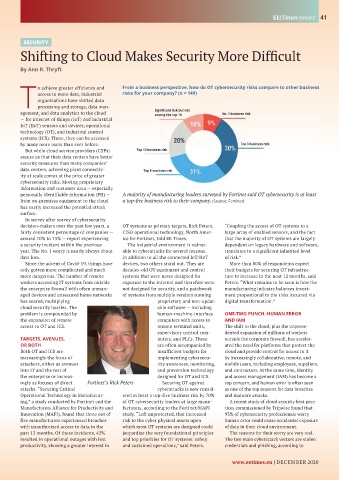
o achieve greater efficiency and From a business perspective, how do OT cybersecurity risks compare to other business
access to more data, industrial risks for your company? (n = 149)
organizations have shifted data
T processing and storage, data man-
agement, and data analytics to the cloud Significant risk but not No. 1 business risk
among the top 10
— for internet of things (IoT) and industrial
IoT (IIoT) sensors and devices, operational
technology (OT), and industrial control
systems (ICS). There, they can be accessed
by many more users than ever before. Top 3 business risk
But while cloud service providers (CSPs) Top 10 business risk
assure us that their data centers have better
security measures than many companies’
data centers, achieving plant connectiv- Top 5 business risk
ity at scale comes at the price of greater
cybersecurity risks. Moving proprietary
information and customer data — especially
personally identifiable information (PII) — A majority of manufacturing leaders surveyed by Fortinet said OT cybersecurity is at least
from on-premises equipment to the cloud a top-five business risk to their company. (Source: Fortinet)
has vastly increased the potential attack
surface.
In survey after survey of cybersecurity
decision-makers over the past few years, a OT systems as primary targets, Rick Peters, “Coupling the access of OT systems to a
fairly consistent percentage of companies — CISO operational technology, North Amer- large array of enabled sensors, and the fact
around 70% to 75% — report experiencing ica for Fortinet, told EE Times. that the majority of OT systems are largely
a security incident within the previous The industrial environment is vulner- dependent on legacy hardware and software,
year. The No. 1 worry is nearly always about able to cyberattacks for several reasons. translates to a significant inherited level
data loss. In addition to all the connected IoT/IIoT of risk.”
Since the advent of Covid-19, things have devices, two others stand out. They are More than 80% of respondents expect
only gotten more complicated and much decades-old OT equipment and control their budgets for securing OT infrastruc-
more dangerous. The number of remote systems that were never designed for ture to increase in the next 12 months, said
workers accessing IT systems from outside exposure to the internet and therefore were Peters. “What remains to be seen is how the
the enterprise firewall with often unman- not designed for security, and a patchwork manufacturing industry balances invest-
aged devices and unsecured home networks of systems from multiple vendors running ment proportional to the risks incurred via
has soared, multiplying proprietary and non-updat- digital transformation.”
cloud security hassles. The able software — including
problem is compounded by human-machine-interface ONE-TWO PUNCH: HUMAN ERROR
the expansion of remote computers with access to AND IAM
access to OT and ICS. remote terminal units, The shift to the cloud, plus the unprece-
supervisory control com- dented expansion of millions of workers
TARGETS, AVENUES, puters, and PLCs. These outside the corporate firewall, has acceler-
OR BOTH are often accompanied by ated the need for platforms that protect the
Both OT and ICS are insufficient budgets for cloud and provide control for access to it
increasingly the focus of implementing cybersecu- by increasingly collaborative, remote, and
attackers, either as avenues rity awareness, monitoring, mobile users, including employees, suppliers,
into IT and the rest of and prevention technology and contractors. At the same time, identity
the enterprise or increas- designed for OT and ICS. and access management (IAM) has become a
ingly as focuses of direct Fortinet’s Rick Peters Securing OT against top concern, and human error is often seen
attacks. “Securing Critical cyberattacks is now consid- as one of the top reasons for data breaches
Operational Technology in Manufactur- ered at least a top-five business risk by 70% and malware attacks.
ing,” a study conducted by Fortinet and the of OT cybersecurity leaders at large manu- A recent study of cloud security best prac-
Manufacturers Alliance for Productivity and facturers, according to the Fortinet/MAPI tices commissioned by Tripwire found that
Innovation (MAPI), found that three out of study. “Left unprotected, that increased 93% of cybersecurity professionals worry
five manufacturers experienced breaches risk to the cyber physical assets upon human error could cause accidental exposure
with unauthorized access to data in the which most OT systems are designed could of data in their cloud environment.
past 12 months. Of those incidents, 42% jeopardize the very foundational principles The reasons for their worry are very real.
resulted in operational outages with lost and top priorities for OT systems: safety The two main cyberattack vectors are stolen
productivity, showing a greater interest in and sustained operations,” said Peters. credentials and phishing, according to
www.eetimes.eu | DECEMBER 2020